When we talk about Web3 social media and platforms, we would inevitably come across the term “DID” (Decentralized Identity¹). Since the concept of DIDs is still very nascent, many people might not fully grasp what DID entails. Therefore, this article serves to address some of the common misconceptions, and at the same time, give you a better technical idea of DIDs in Web3.
The Next.ID community would like to encourage active discussion through the following series of articles:
What feature or system of DID do users benefit most from?
What are the user migration costs for moving from Web2 to Web3?
What can DIDs offer to users in Web3 that is unachievable in Web2?
Is MetaMask a form of DID?
MetaMask’s current monthly active users (MAU) are approximated to be > 30 million. With this large user base, many projects naturally would want to create an identity layer through MetaMask. However, given that MetaMask is merely a wallet with no DID applications, this idea would not work.
Metamask is an EOA-like (Externally Owned Address) wallet. One of the biggest problems surrounding the use of such wallets is the risk of users losing all of their digital assets if their private key or seed phrase gets lost or compromised.
As long as MetaMask fails to solve this pain point, Web3 adoption would still be a huge curveball.
Let’s take a step back and take a look at some of the immediate problems of Web3 identities.
Web3 needs to find a solution for wallet recovery
Using a simple analogy here. Each individual has a name and unique ID number (or driver’s license or passport) in Web2 analogous to the public and private keys of Web3 respectively.
If a Web2 user loses his ID card, by the analogy of private keys, he will still be able to apply for a new ID card through one of the centralized certification bodies (i.e. national public security authorities) and his corresponding assets will not be lost.
Web3 also needs to do the same. How can the user regain control of his account through a decentralized authentication network, even after the loss of the private key? If there is a method to do so, Web2 to Web3 migration will be much easier.
Seed phrases are cumbersome in Web3
As we all know, whenever we create a brand new wallet on different dApps and platforms, we would be given different recovery phrases to jot down. We are told to not lose them as it will risk losing all assets in that wallet.
With so many wallet addresses, private keys, and seed phrases to remember, it surely is a very unpleasant user experience.
There needs to be a decentralized Web3 version of 1Password or LastPass to aid users in better wallet management.
So what’s the problem? Let’s go back to the Web2 world and think about it.
A wallet like MetaMask is essentially like a bank account, which is used to conduct financial transactions. We can only open a new bank account using a unique ID like an ID number (or driver’s license or passport). However, if one takes a Citibank account and requests withdrawals at Standard Chartered, it would simply not work.
This is because the user “identity” and “bank account” are not the same thing.
Recently, the Ethereum community passed the proposal of EIP-2938 — using “Account Abstraction” for the development of smart contract wallets. Another popular DID product, UniPass, also takes a similar approach.
We are seeing more proponents of decoupling the “identity” (public-private key pair) from the “bank account” (abstracted account, wallet address) and building a completely new mechanism. Below are some potential solutions to the aforementioned idea.
Generating a new private key for the one that was previously lost. Some potential methods may include:
Social recovery — A way to guarantee wallet ownership through high-quality on-chain interaction with friends and connections who are able to justify on your behalf.
Backup questions — A series of private and security questions can be used to assist in recovering the private key of the wallet. For example, what was the name of my childhood pet, who was my high school English teacher, etc.
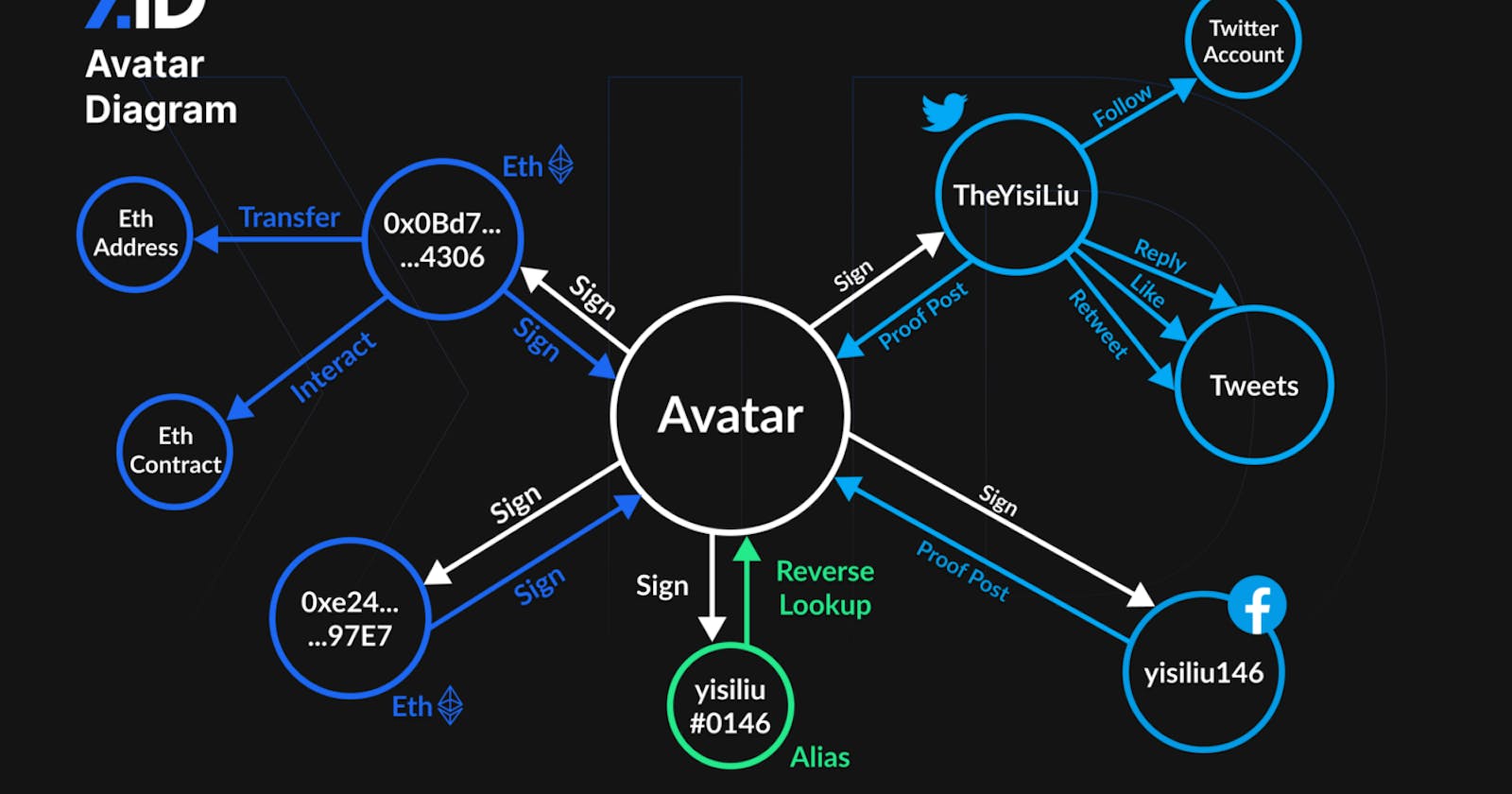
The management of all related Account Abstraction (Web2 IDs and Web3 Abstracted Accounts) can be directly bound and collected into a digital identity (public-private key pair). This is what we call “Avatar” in Next.ID. As shown in the diagram below.**
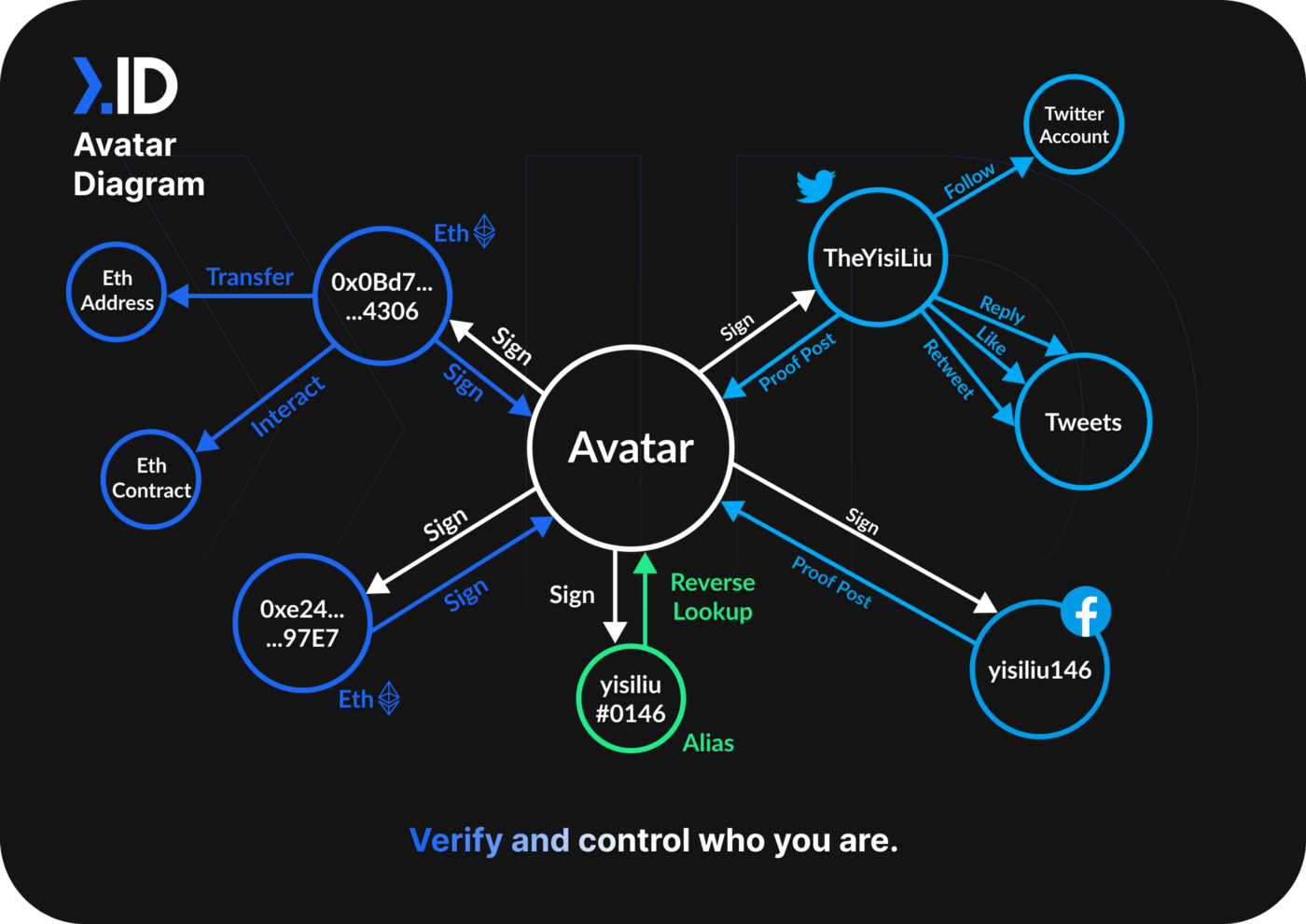
So far, we have touched on the foundational layer of defining DIDs with a “public-private key pair”. In the aspect of DID private key management, we would need the help of the greater Web3 community to explore together the use of social recovery and personal privacy quizzes to lower the barrier to user adoption.
Have we truly considered the proper use of DID before?
Back in Aug 2022, the regulatory sanctions of Tornado Cash (TC) brought upon by the U.S OFAC had caused much fear and uncertainty amongst many Web3 practitioners. Wallet addresses that interacted with TC had been frozen. Even wallet addresses that did not specifically use TC but unknowingly had crypto transferred over to them from another wallet address that used TC, had their wallets frozen. This incident made people question if Web3 is truly resistant to censorship.
At the same time, many DID projects in the market are nonchalant with their services. They are blatantly disregarding the potential risks of leaking personal information, rushing to ship imperfect products for the sake of chasing the hype, and putting no long-term progressional thoughts into it. Given that Web3 privacy protection technology (e.g ZK proofs) has not yet fully matured, we should not expose ourselves to such flaws, putting ourselves in danger of getting another regulatory sanction. If another incident were to arise from exposing the flaws of DID in a regulatory manner, it could get rather embarrassing.
Are DID projects overly focused on external clients and neglecting the needs of users?
From the user’s point of view, the overall implementation of a DID system should go beyond the foundational layer of defining DID identity as the public-private key pair, as discussed earlier.
In order to properly integrate DIDs, it needs to achieve the same level of interoperability and user-friendliness, similar to Web2 counterparts like OpenID/OAuth. It needs to be as simple as possible whereby only a few clicks are needed to complete logins.
Also, all Web2 (e.g. Twitter and Instagram) and Web3 accounts (e.g. Abstracted Accounts and Smart Contract Wallets) should be aggregated under the premise of protecting user privacy. If the user chooses to be anonymous/pseudonymous on their Web2 accounts, there should not be any way to reveal his identity. Ultimately, they can only be traced to an online virtual identity — a string of alphanumeric characters.
What kind of Web3 “one-click login” do users need?
In the Web2 era of apps, every user is familiar with using the one-click log-in. Easy to use and no more annoying passwords.
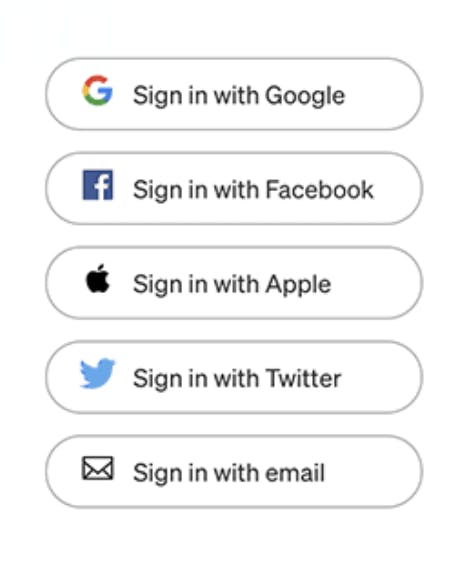
Advantages
- Password required for the first registration.
- Subsequent logins can always use Google, Facebook, Email, etc.
Disadvantages
Users do not have ownership of their own data and they are putting their private info at risk by giving full control of it to the platforms.
Users are bombarded with all kinds of forced advertising as most platforms heavily rely on advertisements to generate revenue and sell user info to these advertisers
With the help of Web3, the issue of data sovereignty can be solved. However, the user experience of dApps in Web3 is not user-friendly and still remains to be improved. It needs to achieve somewhat the same level as the experience we have on Web2 apps if we ever want to talk about user adoption.
Potential improvements in Web3 user experience
AuthService — The Next.ID community has come up with a new idea to improve the UX in Web3 social account interactions. It is designed with the following flow.
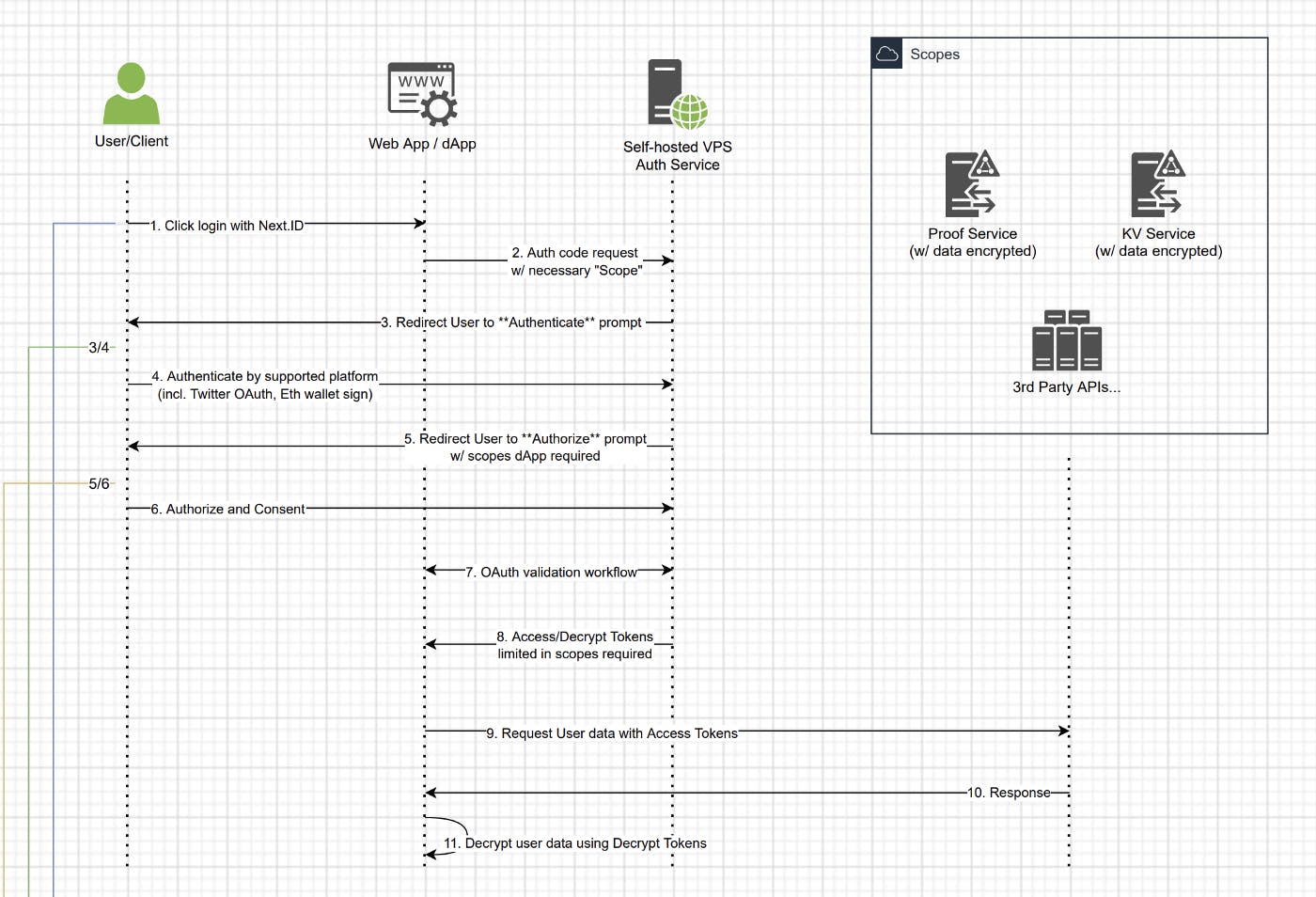
Flowchart for Next.ID’s AuthService
- Users can leverage Next.ID’s AuthService SDK for dApp account authorization operations. The data sources are bound to Next.ID’s in-house ProofService.
- The authorization operation is verified by a VPS (Virtual Private Server) deployed by the user.
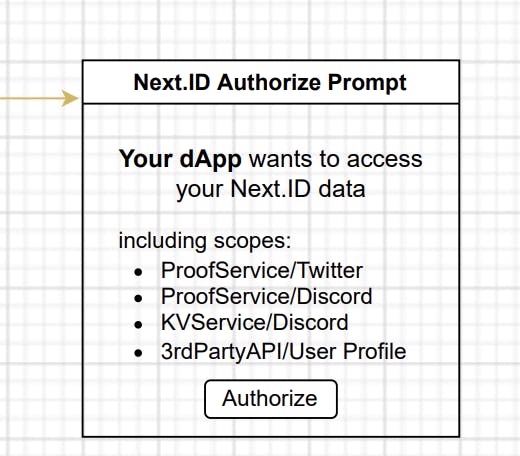
- Upon successful authorization, the user will specify the “scope” to reveal private info related to the user account.
The key 1st step is to use Next.ID when logging into the dApp.
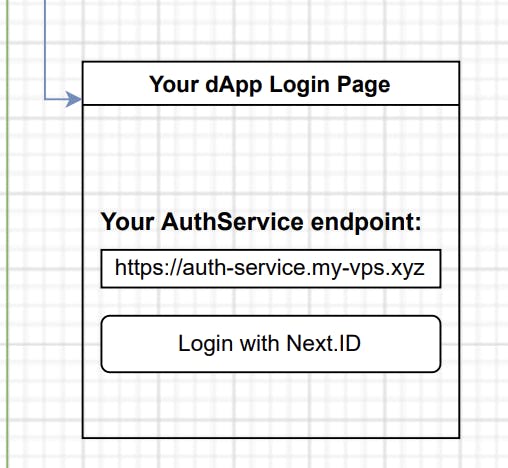
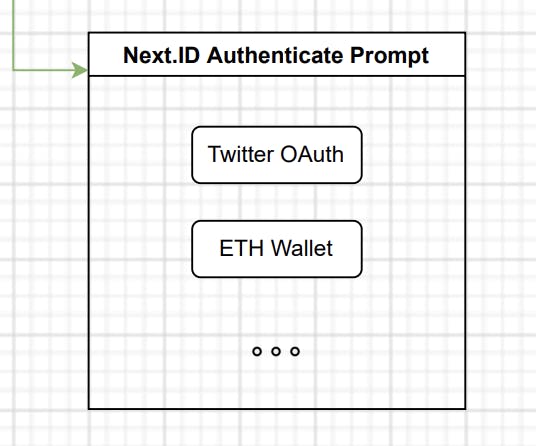
The next step would be to access the authorized account’s data (Wallet ID, Twitter Authentication, etc.). (Step 3 as shown in the main diagram)
Finally, the data of the account gets released (Steps 5 & 6 as shown in the main diagram)
In the subsequent articles, we will dive deeper into the topics related to “privacy” and “security”, and also further explain the VPS (Virtual Private Server) idea behind AuthService.
Thank you for reading and feel free to comment and reblog — the Next.ID open source community warmly invites you to join us in promoting the DID ecosystem.
[1] W3C’s definition of DID is “Decentralized Identifier”. In the Web3 social space, “Decentralized Identity” is used instead for better commercial and product context.
Official Site:next.id
Twitter: @nextdotid
Github:github.com/nextdotid
Discord: bit.ly/NextID_Discord_Official
Biweekly Community Call Recording:
YouTube (EN): youtube.com/channel/UC17C9xWKp0h_pZhfxbNtHsg
Bilibili (CH): space.bilibili.com/1004643496